A Guide to Building Your Vendor Risk Management Framework
Build a robust vendor risk management framework with our step-by-step guide. Learn to mitigate third-party risks and protect your business.
Tired of nonsense pricing of DocuSign?
Start taking digital signatures with BoloSign and save money.
A vendor risk management framework is the strategic playbook your organization uses to find, evaluate, and handle the risks that come with using third-party vendors. It’s not just a checklist you run through once. It’s a living, breathing process designed to protect your operations, data, and reputation before, during, and after you start working with a partner.
Think of it like the architectural plan for a skyscraper. Without a solid blueprint dictating every step, the whole structure is at risk of collapse when the unexpected happens. Your vendor ecosystem is no different.
Why a Vendor Risk management Framework Is Mission-Critical

In today’s interconnected business world, your vendors are a true extension of your company. Whether it's a cloud software provider, a logistics partner, or a marketing agency, these third parties often get access to your most sensitive data and critical systems. This deep integration is great for efficiency, but it also opens doors to serious risks that can’t be ignored.
A single weak link in your supply chain can trigger a domino effect. A data breach at a small, seemingly insignificant vendor can lead to massive regulatory fines for your company, shatter your hard-earned reputation, and bring your operations to a grinding halt. The numbers don't lie—studies show that breaches involving a third party have doubled, now accounting for a staggering 30% of all data breaches.
This highlights a tough reality: managing your own security is only half the battle. You have to manage your vendors' security, too.
The Foundation for Secure and Efficient Operations
A formal vendor risk management framework gives you the structure needed to protect your business from the outside in. It helps you shift from a reactive, chaotic approach to a proactive, organized one. Instead of scrambling when a vendor has a security incident, you have a predefined process ready to go for every stage of the relationship.
This kind of framework is essential for a few key reasons:
- Regulatory Compliance: Mandates like HIPAA, GDPR, and the ESIGN Act don't just apply to you; they require you to ensure your vendors handle data securely. A framework provides the auditable proof you need to meet these standards.
- Operational Resilience: It forces you to understand and plan for potential disruptions, ensuring your business can continue running if a critical supplier suddenly goes offline.
- Reputation Management: Protecting customer data is non-negotiable. A breach that originates from a vendor can erode customer trust just as fast—or faster—than one that happens internally.
Setting the Stage for Modern Contract Management
At the heart of every single vendor relationship is a contract. A strong vendor risk management framework ensures these agreements contain the right safeguards from the very beginning. But trying to manage all these contracts manually with spreadsheets and email is slow, messy, and a recipe for mistakes.
This is where a unified platform like BoloSign becomes so valuable. You can create, send, and sign PDFs instantly, ensuring you’re not just moving faster—you're executing a key part of your risk strategy. With BoloSign, you can build pre-approved templates that align perfectly with your risk policies, making sure every contract is compliant from day one. Our AI-powered contract review can even help you spot risky clauses before they become a liability.
By integrating a secure digital signing solution directly into your VRM process, you build a seamless workflow that is both fast and secure. From a healthcare provider onboarding a new software vendor under strict HIPAA rules to a real estate firm engaging contractors for a new project, the need for a reliable, risk-aware contract process is universal.
A well-designed VRM framework establishes the rules of engagement. Modern tools like BoloSign provide the automation and security to enforce those rules efficiently, turning policy into practice without slowing down your business.
Ultimately, building this framework is the first and most important step toward creating a secure and scalable vendor ecosystem. It sets the foundation for every interaction, ensuring that as your business grows, your risk exposure stays firmly under control.
The Essential Pillars of an Effective VRM Framework
A powerful vendor risk management framework isn’t some dusty binder sitting on a shelf. It's a living, breathing system of interconnected practices that work together to shield your business from harm. Think of it like building a fortress; each pillar is a critical wall that reinforces the others, creating a complete defense system.
Let's break down the six essential pillars you need to construct a framework that's both solid and practical.
Strong Governance and Policy
This is your foundation. Governance defines the "rules of the game" for your entire vendor ecosystem. It’s where you formally state your organization's risk appetite—how much risk you are willing to accept—and establish clear policies, roles, and responsibilities for everyone involved, from procurement to legal and IT.
Without strong governance, your vendor management efforts will be chaotic and inconsistent. A clear policy ensures everyone understands their duties and makes decisions that align with the company's strategic goals.
Thorough Vendor Due Diligence
Before you even think about signing a contract, you need to know exactly who you're getting into business with. This is the due diligence pillar, a deep-dive investigation into a potential vendor's financial stability, security practices, and compliance record. It’s just like running a background check before hiring a key employee.
For a staffing agency, this might involve verifying a payroll software vendor's data security certifications. A healthcare clinic would need to confirm a new partner's HIPAA compliance. This initial screening is your first line of defense, keeping high-risk vendors from ever entering your ecosystem. Implementing these checks requires a solid grasp of core vendor management best practices that guide the vetting process.
Strategic Risk Tiering
Not all vendors pose the same threat, so they shouldn't be treated the same way. Risk tiering is the practical process of categorizing vendors based on the level of risk they introduce to your business. A vendor with access to sensitive customer data is high-risk, while a supplier providing office stationery is low-risk.
By segmenting vendors into tiers (e.g., Critical, High, Medium, Low), you can focus your limited resources where they matter most. This ensures your most critical partners receive the highest level of scrutiny, making your entire program more efficient and effective.
Ironclad Contractual Safeguards
The contract is where your risk policies become legally binding. This pillar involves embedding specific safeguards directly into your vendor agreements. These are the clauses that protect you if something goes wrong, covering everything from data security requirements and liability limits to service level agreements (SLAs) and the right to audit.
This is where contract automation really shines. Instead of starting from scratch, you can use a platform like BoloSign to instantly generate contracts from pre-approved, compliant templates. This ensures every agreement, whether for a real estate transaction or a new logistics partner, contains the necessary protections. With our AI-powered contract review, you can even flag risky terms before sending a contract out for signature. For an even deeper look, explore our complete guide to vendor management best practices.
Continuous Monitoring
Signing the contract isn't the finish line; it's the starting gun. The world changes, and so do your vendors' risk profiles. Continuous monitoring is the pillar that ensures you stay ahead of emerging threats. This involves regularly reviewing vendor performance, checking for new security vulnerabilities, and staying aware of any changes in their financial health or compliance status. It’s an ongoing process, not a one-time check.
Secure Offboarding
Every vendor relationship eventually comes to an end. A secure offboarding process is crucial for closing the loop and preventing risks from lingering. This pillar involves a structured checklist to ensure all access to your systems and data is revoked, all company assets are returned, and final payments are settled correctly. A clean offboarding protocol protects your sensitive information long after a vendor is gone.
Your 5-Step Blueprint for Implementing the Framework
Knowing the theory behind a vendor risk management framework is one thing, but actually putting it into practice is a completely different ballgame. Moving from a plan on paper to a real-world program can feel overwhelming, but a structured roadmap breaks the whole process down into five manageable steps.
Think of this as your blueprint for getting a VRM program off the ground and running effectively.
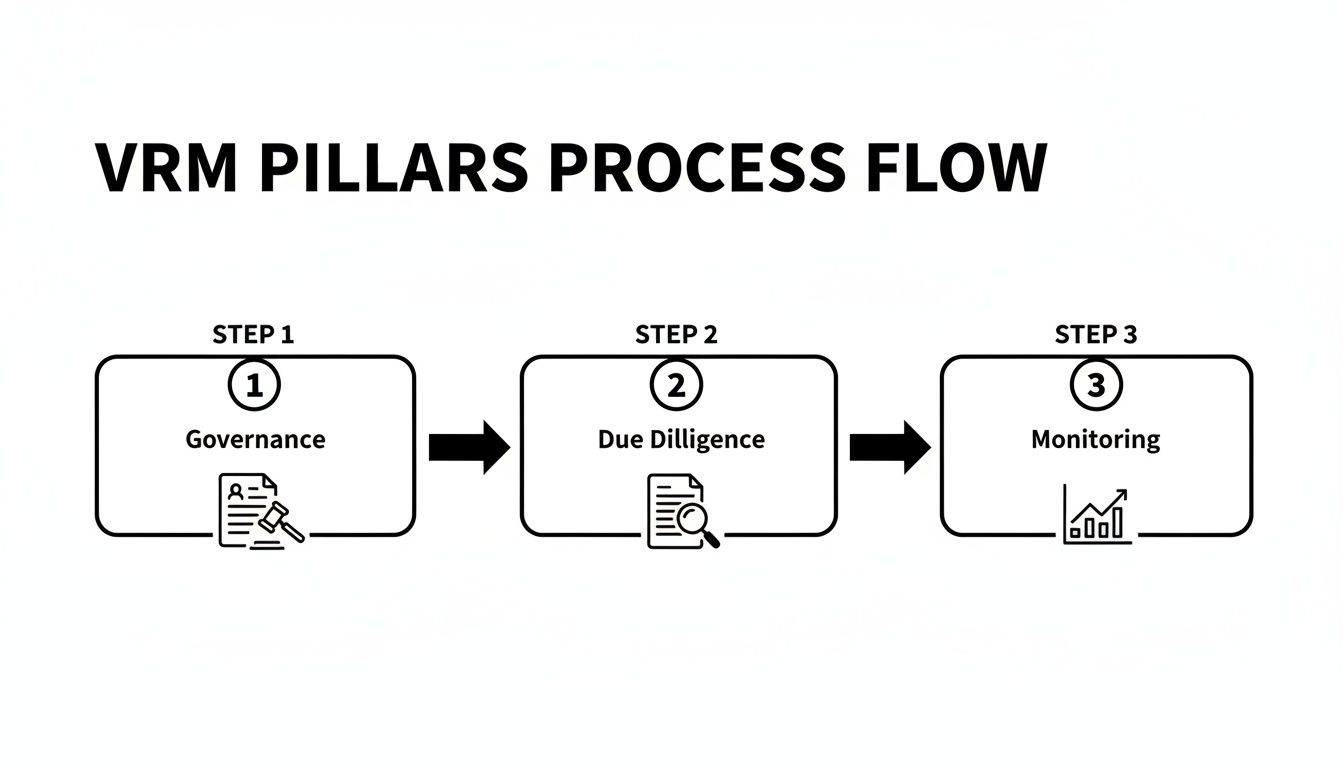
As you can see, these pillars aren't a one-and-done sequence. They're interconnected functions that have to work in sync to truly protect your organization.
Step 1: Define Your Risk Tolerance and Governance
First things first: you have to set the rules of the game. Your organization needs to formally decide on its risk tolerance—that is, the level and type of risk it’s willing to accept from third parties. This isn’t a decision for one person; it requires a cross-functional risk committee with leaders from legal, IT, finance, and procurement.
Once you’ve defined that tolerance, it becomes the bedrock of your official VRM policy. This document should spell out everyone's roles, responsibilities, and the exact procedures for every stage of the vendor lifecycle. It creates a single source of truth that will guide every decision you make from here on out.
Step 2: Create a Centralized Vendor Inventory
You can't manage what you don't know you have. The next critical step is to build a single, centralized inventory of every vendor you work with. This is way more than just a list of names. For each partner, you need to capture key details like:
- Contact Information: Who’s your main point of contact for day-to-day operations versus a security incident?
- Services Provided: What critical function does this vendor actually perform for your business?
- Data Access: What kind of data do they touch, process, or store? Is it sensitive?
- Contract Details: When is the current agreement up for renewal? What are the terms?
This exercise almost always uncovers a surprising number of unmanaged or "shadow IT" vendors, immediately showing you where your biggest risks are hiding.
Step 3: Develop a Practical Risk Tiering System
With your vendor list complete, you can start sorting them into risk tiers. This simple step is a game-changer because it lets you focus your time and energy where it matters most. A four-tier system usually works perfectly:
- Critical: Vendors whose failure would bring your business to an immediate and screeching halt.
- High: Vendors with access to sensitive data (like PII or PHI) or those connected to critical IT systems.
- Medium: Vendors providing important but non-critical services that keep the lights on.
- Low: Vendors with zero access to sensitive data or systems, like your office coffee supplier.
How you tier a vendor directly determines how deep your assessment goes and how often you check in on them. Your critical vendors will get the full, exhaustive due diligence treatment and constant oversight, while the low-risk ones might just need a quick check-up once a year.
Step 4: Standardize Assessment and Onboarding Workflows
Consistency is the key to a VRM program that can actually scale. In this step, you need to standardize the entire workflow for assessing and onboarding new vendors. This means creating a repeatable process covering security questionnaires, document reviews, and—most importantly—contract execution.
This is where manual processes fall apart, creating frustrating bottlenecks and introducing human error. A contract automation platform like BoloSign can completely transform this stage. You can create, send, and sign PDFs online using legally pre-approved templates that automatically align with your risk policies.
For example, a logistics company in the UAE can use a template with specific clauses for customs and compliance already included, ensuring every partnership is set up correctly. This kind of automation removes the guesswork and makes secure onboarding much faster. Find out more about how our powerful AI contract review features can strengthen this process even further.
Step 5: Establish Continuous Monitoring and Reporting
A vendor’s risk profile isn't set in stone; it’s constantly changing. Your final step is to build a system for continuous monitoring and clear, concise reporting. This means setting up alerts for negative news, tracking performance against SLAs, and scheduling periodic reassessments based on each vendor's risk tier.
Effective monitoring turns your VRM framework from a one-time project into a dynamic, ongoing program. It ensures you can proactively identify and mitigate emerging threats before they escalate into costly incidents.
You also need to create straightforward dashboards and reports for leadership. These should track key KPIs, like the number of high-risk vendors assessed or the average time it takes to onboard a new partner. This is how you prove the program's value and effectiveness. Following these five steps will help you build a solid framework that not only protects your business but helps it grow securely.
How AI Contract Automation Fortifies Your Vendor Management
Let's be honest: spreadsheets and scattered email chains are the weakest links in any modern vendor risk management framework. They're slow, riddled with human error, and create dangerous blind spots. When vendor contracts are buried in inboxes and critical risk data lives in disconnected files, keeping a consistent watch over your partners is nearly impossible. This manual approach doesn't just slow you down; it actively puts your business at risk.
This is where smart, AI-powered platforms change the entire game. By swapping manual grunt work for intelligent automation, you can enforce your governance policies every single time, speed up onboarding, and get a clear, real-time picture of your entire vendor ecosystem.
From Manual Chaos to Automated Control
The shift away from these outdated methods is already well underway. Recent data shows that 64% of organizations now use dedicated software for third-party risk management, a huge jump from the previous year. But there are still big gaps—nearly half of companies admit their current tools can't properly evaluate risk across the entire vendor lifecycle.
This is exactly the problem a platform like BoloSign was built to solve. It moves you from high-risk, hands-on work to low-risk, automated control. Let's look at what that means in the real world.
Manual VRM vs AI-Automated VRM with BoloSign
The table below paints a clear picture of how an AI-driven contract platform transforms each stage of the vendor management process, turning risky manual steps into secure, automated workflows.
| VRM Stage | Manual Process (High Risk) | Automated with BoloSign (Low Risk) |
|---|---|---|
| Contract Creation | Teams use outdated or incorrect templates, introducing legal inconsistencies. | Generate agreements from pre-approved, compliant templates to enforce governance. |
| Risk Review | Key risks in vendor-supplied contracts are missed by overwhelmed legal teams. | Use AI-powered contract review to instantly flag non-standard or risky clauses. |
| Approval Workflow | Approvals are chased via email, leading to delays and missed steps. | Route contracts automatically to the right stakeholders for approval, creating an audit trail. |
| Execution | Printing, scanning, and mailing contracts takes days or weeks. | Sign PDFs online instantly with secure, legally binding eSignatures (ESIGN & eIDAS compliant). |
| Monitoring | Contracts are stored in various locations, making it impossible to track renewals or obligations. | A centralized, searchable repository provides full visibility for easy monitoring and audits. |
As you can see, the difference isn't just about speed—it's about building a fundamentally more secure and reliable system from the ground up.
Strengthening VRM in the Real World
Think about a professional services firm in Canada that needs to onboard a new software subcontractor. This is a high-stakes relationship governed by strict data privacy and intellectual property rules, a central pillar of their vendor risk management framework.
With a manual process, the firm would email contract drafts back and forth, just hoping the right IP protection clauses are included. The legal team would have to read every single line to confirm compliance, a process that could drag on for weeks.
Now, let's see how BoloSign transforms that workflow:
- Creation: The project manager instantly generates the contract using a pre-approved template that automatically includes mandatory confidentiality and data handling clauses. No guesswork involved.
- Review: BoloSign’s AI contract review scans the agreement, making sure all required IP protection clauses are present and flagging any unusual liability terms the subcontractor tried to add.
- Execution: Once approved, the contract is sent for digital signing. Both parties can sign the document securely online in just a few minutes, confident that the process is fully compliant.
- Storage: The finalized, executed agreement is automatically filed in a secure, centralized repository, complete with a full audit trail for any future compliance checks.
This automated process does more than just save time. It actively fortifies the firm’s VRM framework by guaranteeing compliance, cutting down on risk, and creating a perfect, auditable record of the entire transaction. The role of artificial intelligence in contract management is to act as your safety net, catching potential problems before they ever become liabilities.
Measuring the Success of Your VRM Framework
Building a solid vendor risk management framework is a huge win, but getting it live is just the beginning. The real question from leadership will always be: "Is it working?" How do you prove your efforts are actually cutting down on risk, making the business more efficient, and delivering a real return on investment?
The answer is data. Without clear metrics, your VRM program is just a collection of activities. With the right Key Performance Indicators (KPIs), it becomes a strategic asset that speaks a language everyone in the C-suite understands. These numbers don't just justify your program's existence; they shine a light on where to improve next.
Key Metrics That Matter to Leadership
To show your framework is more than just busywork, you need to present concrete numbers that connect directly to efficiency, security, and compliance. Vague statements won't cut it. Here are a few essential KPIs to start tracking:
- Average Vendor Onboarding Time: This is the clock from the first "hello" with a new vendor to the final signature on their contract. Long cycle times can stall critical projects and frustrate your internal teams. The goal here is to shrink this timeline without cutting corners on due diligence.
- Percentage of High-Risk Vendors Assessed: This metric tracks how many of your most critical vendors have gone through a formal risk assessment within a set period, like annually. A high percentage proves your program is focusing its energy on the biggest threats first.
- Number of Vendor-Related Security Incidents: This one is a direct measure of your framework's effectiveness. The ultimate goal is to get this number as close to zero as possible by catching and fixing risks before they turn into real problems.
- Vendor Compliance Adherence Rate: How many of your vendors are actually meeting the rules you set out in their contracts? This KPI tracks adherence to key requirements, like maintaining specific security certifications or insurance levels.
Tracking KPIs with Technology
Trying to pull all this data together manually from spreadsheets and email chains is a recipe for headaches and inaccurate reports. This is where a centralized platform becomes non-negotiable for any serious vendor risk management framework. It gives you a single source of truth for real-time, accurate reporting.
This is exactly why technology like BoloSign is so valuable. With a unified dashboard and immutable audit trails, the data you need is right at your fingertips. You can instantly see contract-related KPIs, like signature cycle times, which directly feed into your average vendor onboarding time. And with our AI-powered contract review, you can automatically verify that mandatory compliance clauses are included, giving you a clear metric for your vendor compliance adherence rate. This kind of insight makes it simple to build reports that show a clear ROI.
The demand for these tools is exploding for a reason. The global vendor risk management market was valued at USD 10.67 billion in 2024 and is expected to more than double to USD 24.95 billion by 2030. This growth is driven by intense regulatory pressure and the sheer complexity of modern supply chains, making effective measurement more critical than ever. Discover more insights about these market trends.
By leveraging a platform that automates data collection, you can spend less time chasing information and more time analyzing it to make strategic decisions. This transforms your VRM program from a cost center into a proven value driver for the entire organization.
Ultimately, measuring success is about telling a story with data—a story of reduced risk, enhanced efficiency, and stronger compliance.
Building a Secure and Scalable Vendor Ecosystem
A successful vendor risk management framework isn't a static project you complete once and file away. It’s a living, breathing process—a continuous cycle of assessment, monitoring, and adaptation that shields your business as it grows. Building a secure and scalable vendor ecosystem means weaving risk awareness into the very fabric of how you choose and manage your partners.
The real takeaway is that every piece, from governance and due diligence to contracting and offboarding, has to work together. Manual processes just can't keep up with the speed and complexity of business today. Technology is no longer a “nice to have”; it’s the essential glue holding your framework together, turning policy into consistent, everyday practice.
From Framework to Foundation with BoloSign
This is where a platform like BoloSign becomes foundational. It’s far more than just a way to sign PDFs online; it’s an integral part of your risk management lifecycle. The journey to a secure vendor relationship starts with a solid, compliant contract.
BoloSign ensures that your risk policies are enforced from the very first step of vendor onboarding. By using pre-approved templates and automated approval workflows, you get rid of the inconsistencies and human errors that open the door to vulnerabilities. For a deeper dive, check out our guide on vendor onboarding best practices.
Our AI-powered features give you an extra layer of defense, helping you spot risky clauses and maintain compliance with standards like ESIGN, eIDAS, HIPAA, and GDPR. The ability to create, send, and execute contracts instantly transforms your onboarding from a lengthy, high-risk ordeal into a secure, efficient workflow. As you build your ecosystem, understanding the nuances of partner selection is key, and resources on choosing an IT outsourcing company can provide valuable context for making informed decisions.
BoloSign acts as the operational engine for your framework, securing your most critical vendor touchpoint—the contract—with speed and intelligence.
We believe that robust security shouldn’t come with a prohibitive price tag. BoloSign offers unlimited documents, templates, and team members at one fixed price, making it up to 90% more affordable than alternatives like DocuSign or PandaDoc.
Ready to see how an AI-powered platform can secure and simplify your vendor contracting? Start your 7-day free trial to experience it firsthand.
Frequently Asked Questions About VRM Frameworks
Jumping into a vendor risk management framework can feel complex, and it's natural for questions to pop up. Here are some straightforward answers to the questions we hear most often from organizations building out their programs.
What Is the First Step in Creating a Framework?
Before you do anything else, you have to establish clear governance. It’s the bedrock of the entire framework.
This means defining your organization's risk appetite—how much risk you're actually willing to take on—and formalizing it in a policy that spells out roles, responsibilities, and the rules of engagement. Pulling together a cross-functional team with leaders from procurement, legal, IT, and finance is the best way to make sure every angle is covered.
Without this strong foundation, everything else you build will be on shaky ground.
How Often Should We Reassess Vendor Risk?
There's no single right answer here—the frequency of your assessments should always match the vendor's risk level. A one-size-fits-all approach is a recipe for inefficiency and can leave you dangerously exposed.
- High-risk vendors, especially those touching sensitive data, need a close eye. Assess them at least annually and keep them under continuous monitoring.
- Medium-risk vendors can typically be reassessed every 18-24 months.
- Low-risk vendors might only need a quick check-in less frequently.
That said, always trigger an immediate reassessment if something major happens, like a security breach on their end or a significant change in the services they provide you.
How Does Contract Automation Improve a VRM Process?
Contract automation software is what turns your vendor risk management framework from a document into a living, breathing process that works at scale. A platform like BoloSign is designed to connect your risk policies to everyday execution.
For instance, it ensures consistency by making sure everyone uses pre-approved legal templates. Its AI can even flag risky terms in a vendor's contract before you sign, preventing headaches down the road.
Automated workflows route contracts to the right people for approval every single time, creating a perfect, unmissable audit trail. It also gives you one central, secure place to store every agreement, which makes ongoing monitoring and future audits much simpler.
A robust VRM framework sets the rules, but contract automation is the engine that enforces those rules efficiently. It’s the bridge between policy and practice, ensuring every single agreement aligns with your risk strategy.
Finally, legally compliant eSignature capabilities (like those adhering to ESIGN and eIDAS) lock down and speed up the final step. It transforms a slow, manual process into a fast, secure, and auditable workflow, letting you create, send, and sign PDFs online with total confidence.
A strong vendor risk management framework is only as good as its execution, and that comes down to secure and efficient contracting. BoloSign provides the AI-powered tools to make it happen, with unlimited documents and team members at a fixed price that’s up to 90% more affordable than other options. See how simple vendor contracting can be by starting your 7-day free trial today.

Paresh Deshmukh
Co-Founder, BoloForms
5 Jan, 2026
Take a Look at Our Featured Articles
These articles will guide you on how to simplify office work, boost your efficiency, and concentrate on expanding your business.

Compare the best AI contract review tools for 2025. See features, benefits, and practical tips to implement them at scale. Explore BoloSign’s unified solution.
Paresh Deshmukh
Co-Founder, BoloSign

Learn if clickwrap agreements are legally binding, how they work, and key best practices for enforceability.
Paresh Deshmukh
Co-Founder, BoloSign
Ready to streamline your contract management with AI?
Contact Sales
AI assistant to draft, review, and eSign contracts on autopilot for fastest growing companies.
Email: support@boloforms.com


Sales Inquiry

AI assistant to draft, review, and eSign contracts on autopilot for fastest growing companies.
Email: support@boloforms.com


Company
Solutions
Resources
Legal & Security
Sales Inquiry